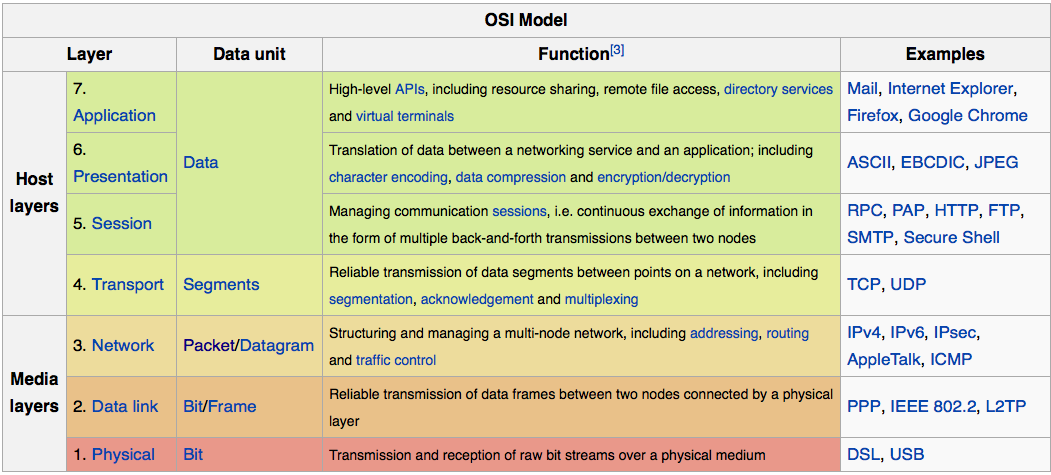
Sensors | Free Full-Text | Physical Layer Authentication in Wireless Networks-Based Machine Learning Approaches

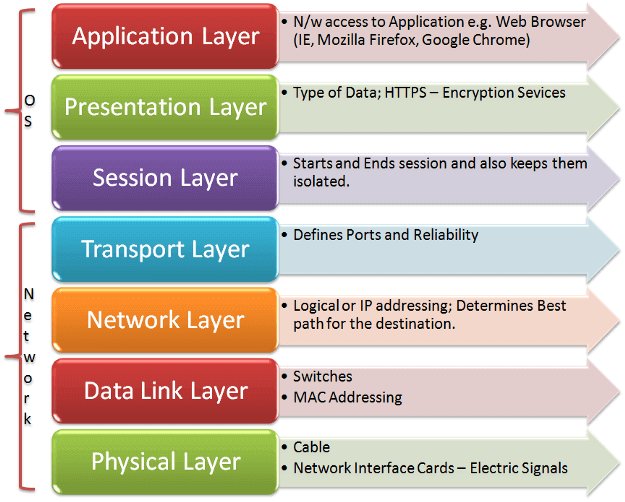
Attack vectors w.r.t OSI Layers. Here's a short summary of different… | by Rohan Krishnamurthy | CodeX | Medium

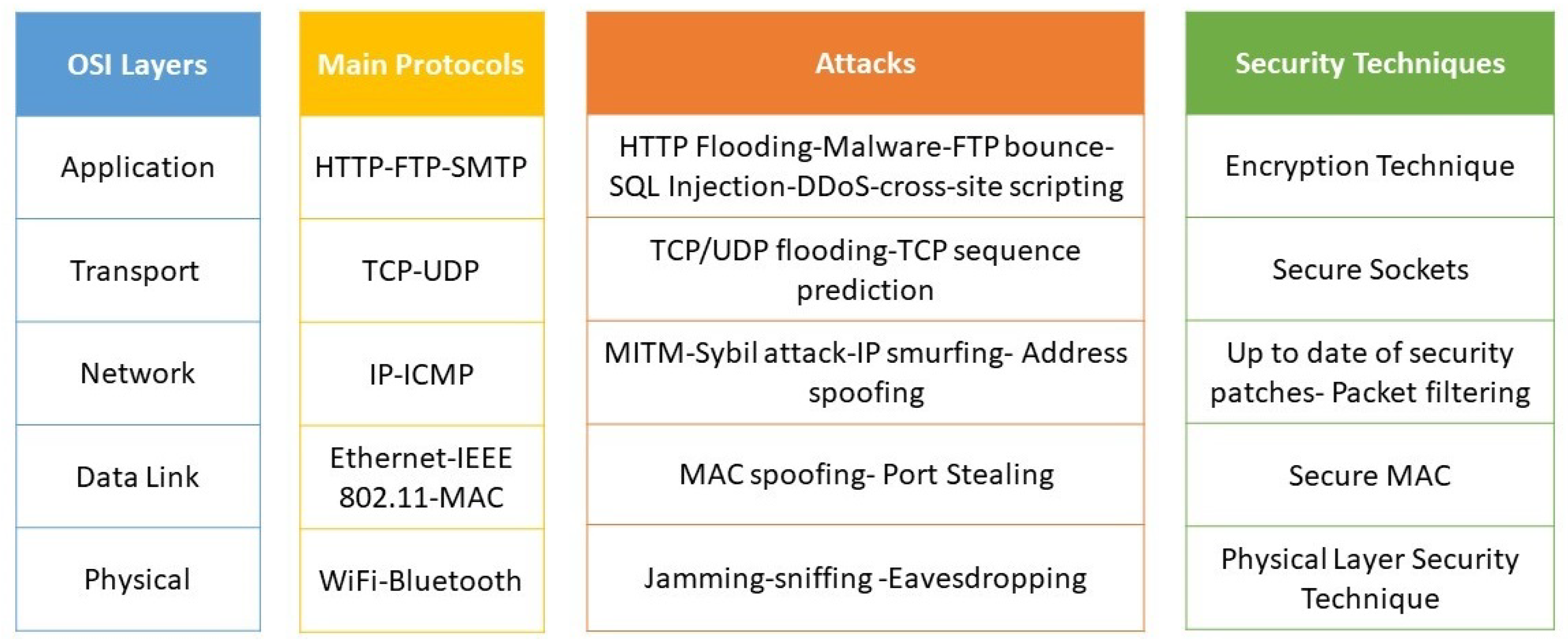
Denial of service attacks in edge computing layers: Taxonomy, vulnerabilities, threats and solutions - ScienceDirect

Cyber Security Feed on X: "RT @CyberSecOb: Attack Possibilities by OSI Layer – Datalink Layer Available for download in Press Quality: https://t.co/3rO7e3CnDD For fur…" / X



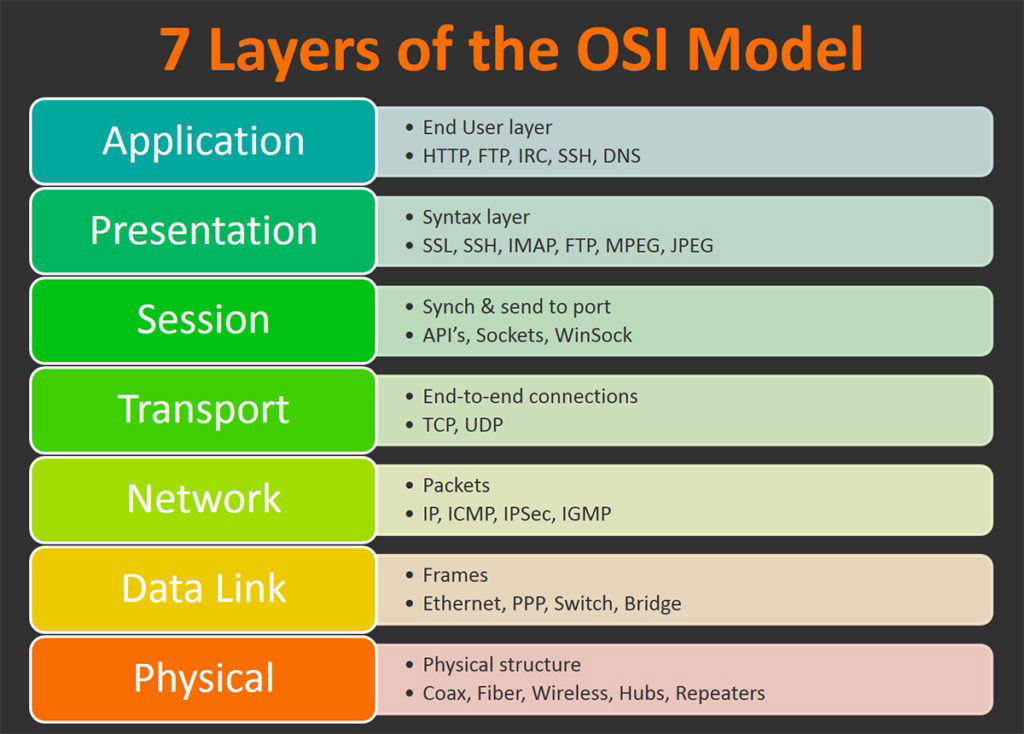
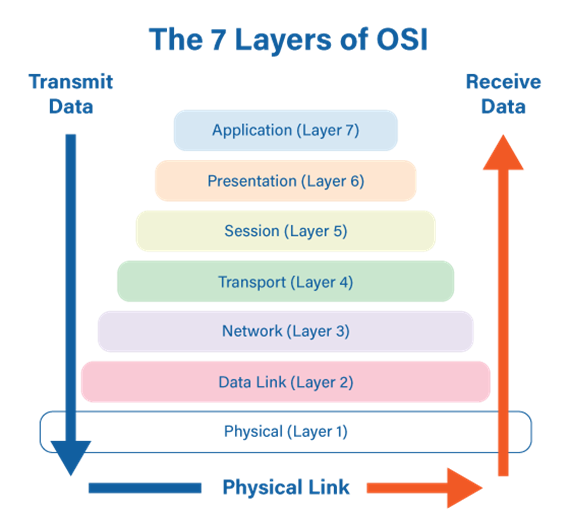
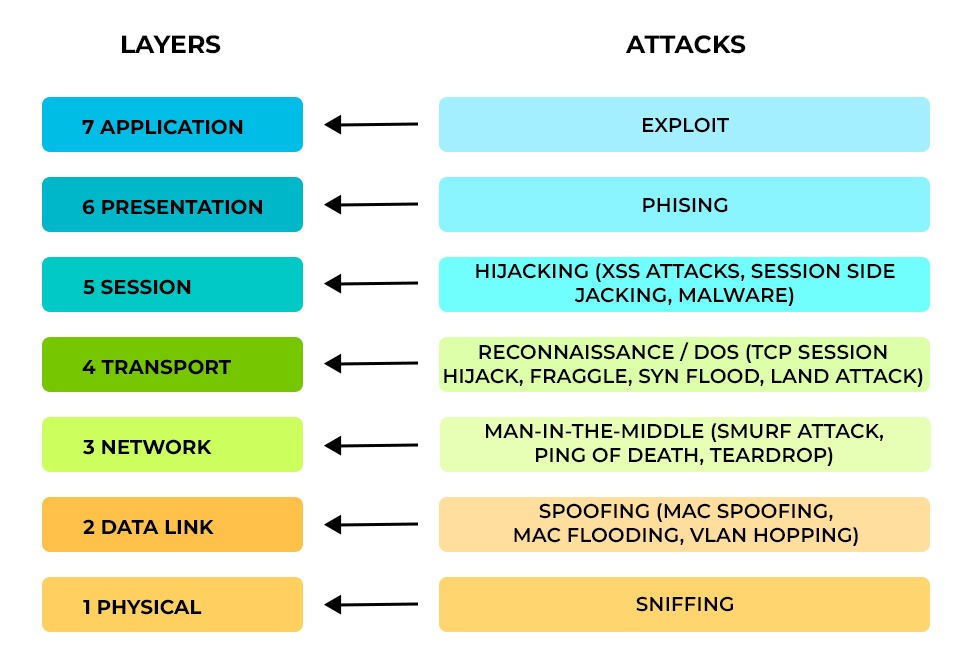


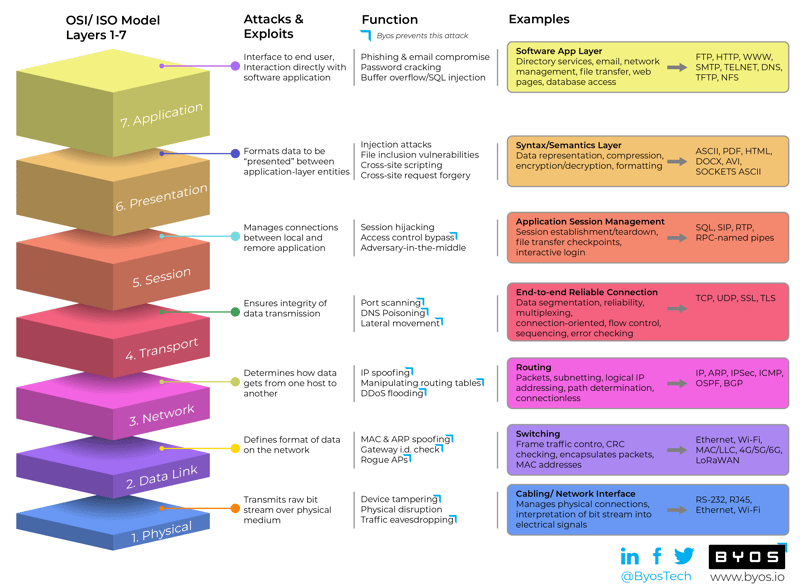




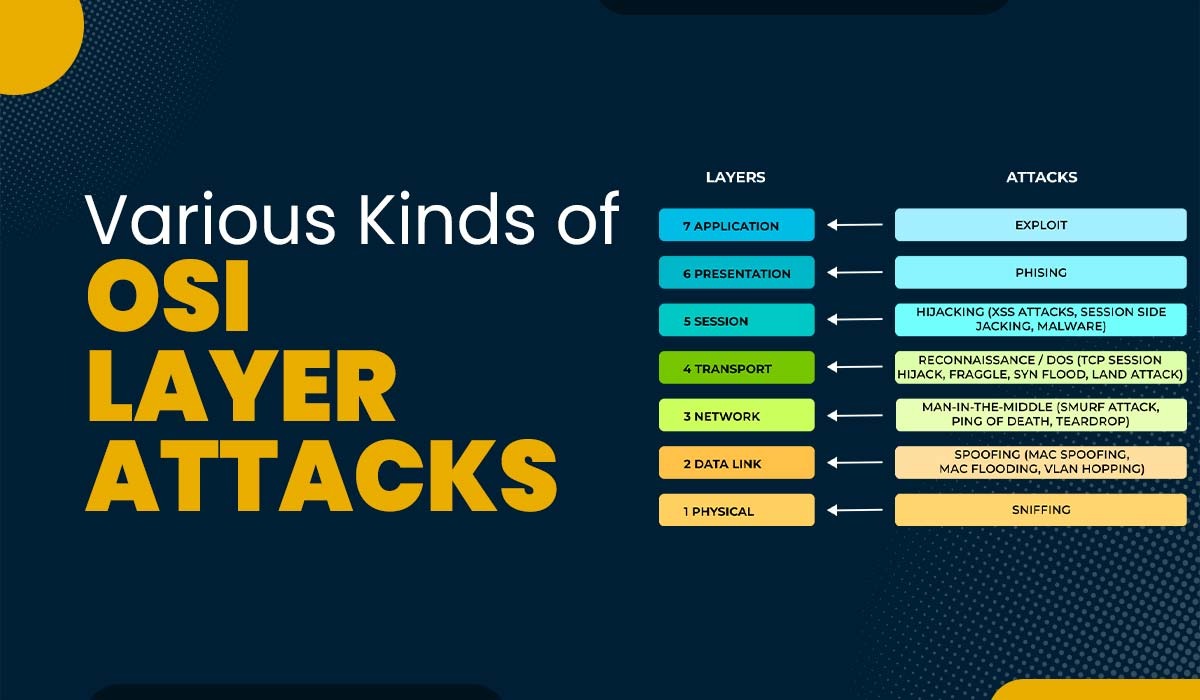
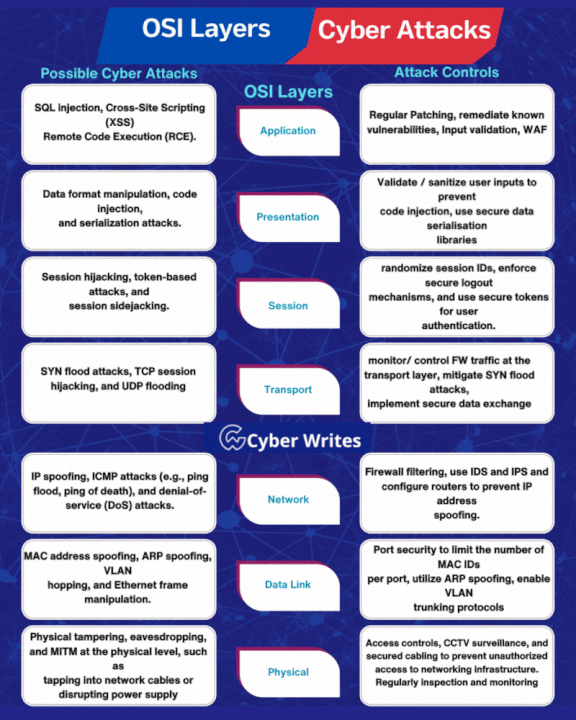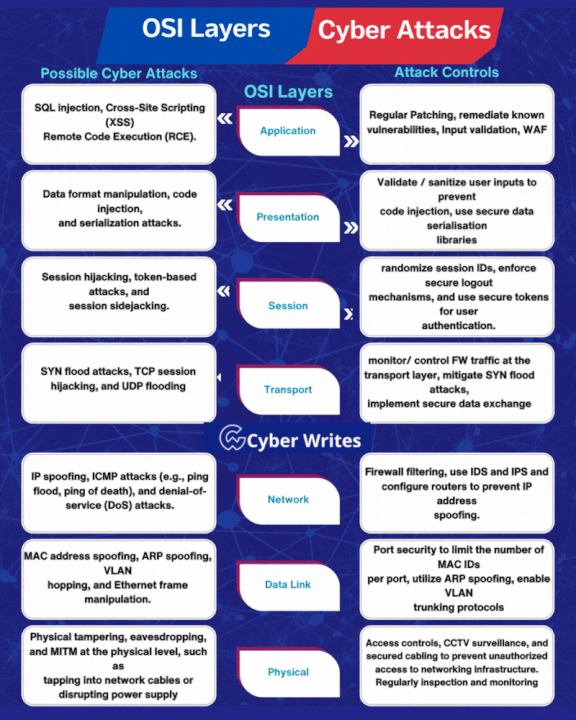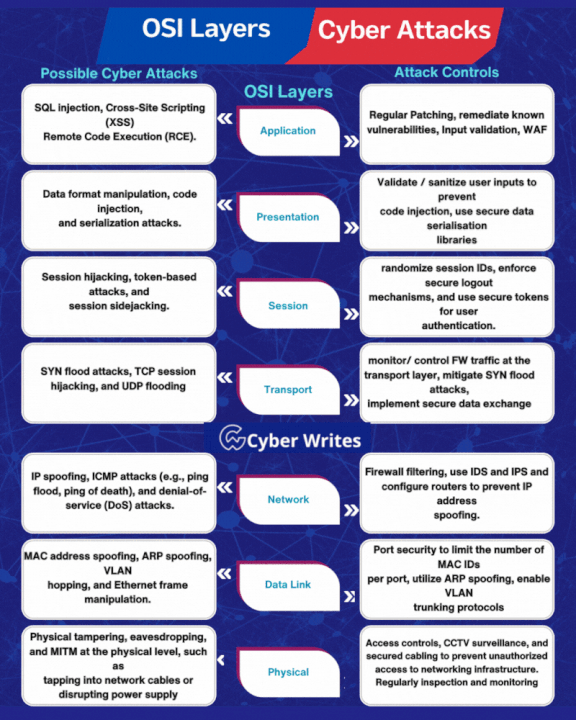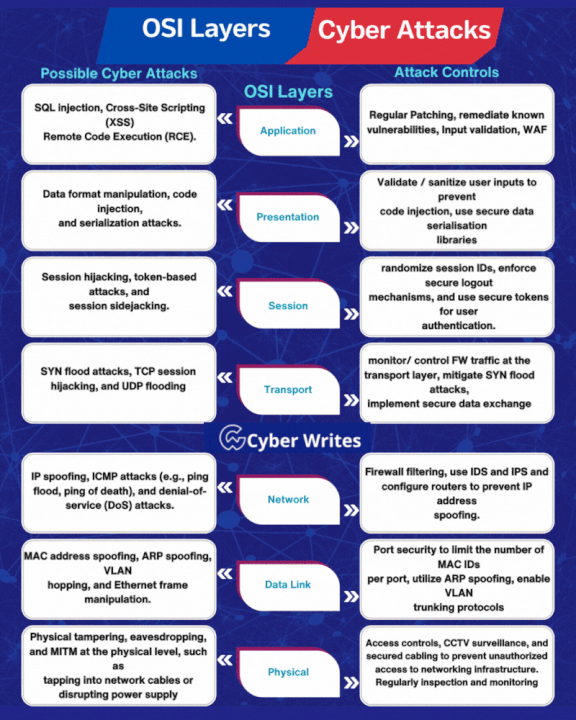
.png)