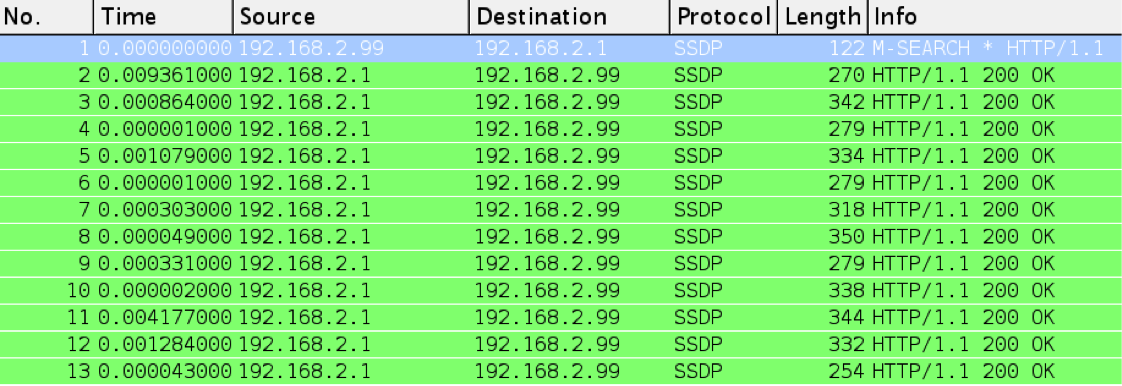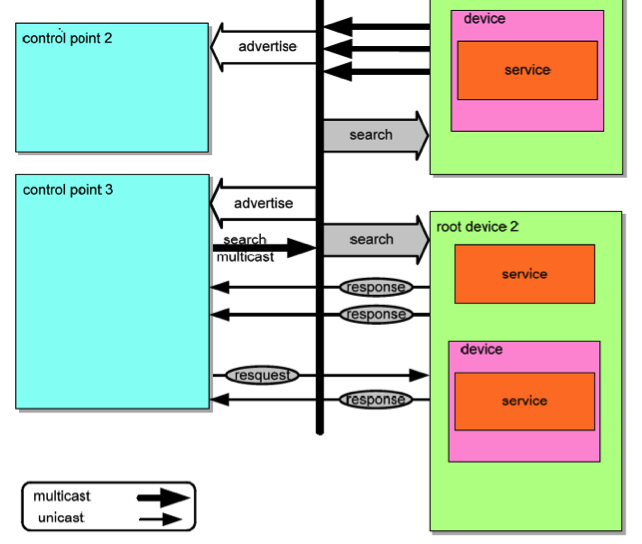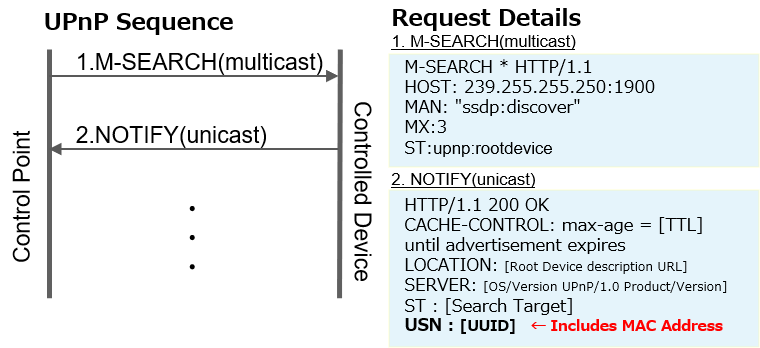
Identify Mirai Variant Infected Devices from SSDP Response - JPCERT/CC Eyes | JPCERT Coordination Center official Blog
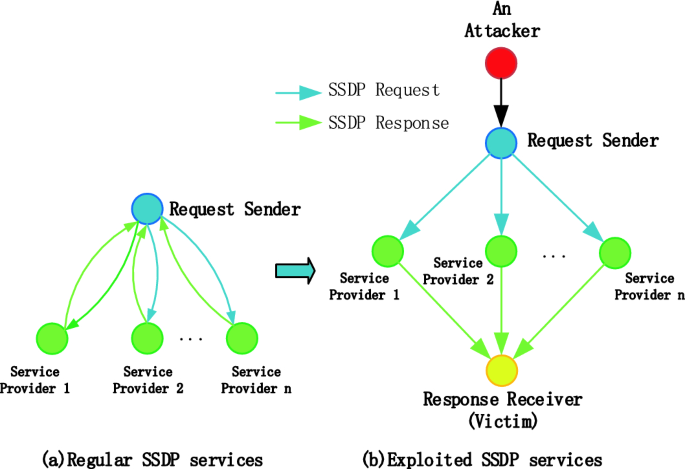
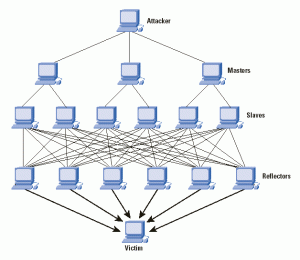
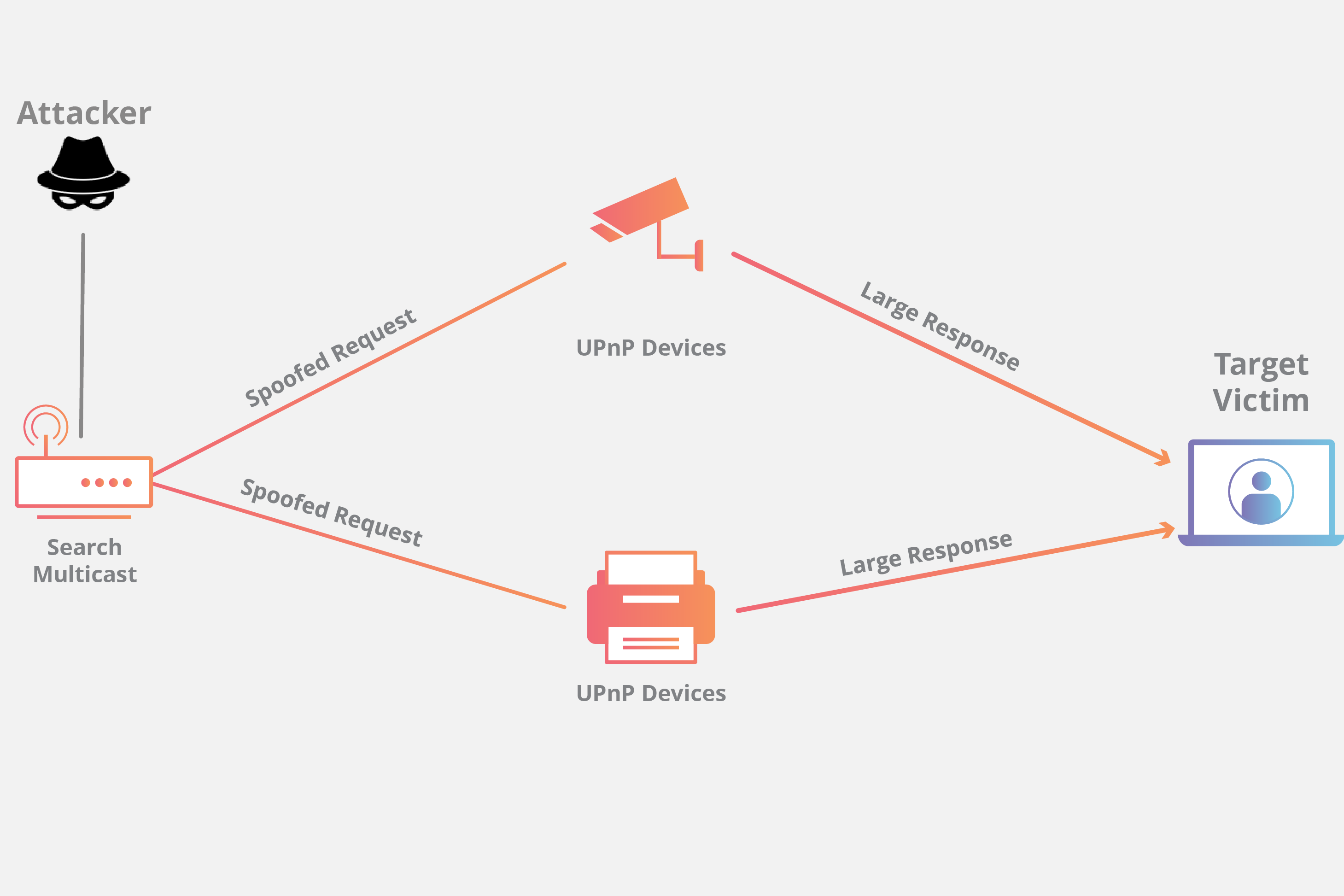
A Multi-location Defence Scheme Against SSDP Reflection Attacks in the Internet of Things | SpringerLink

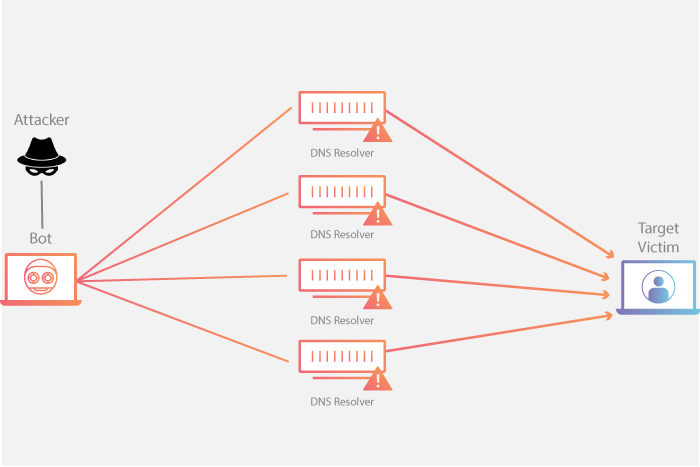
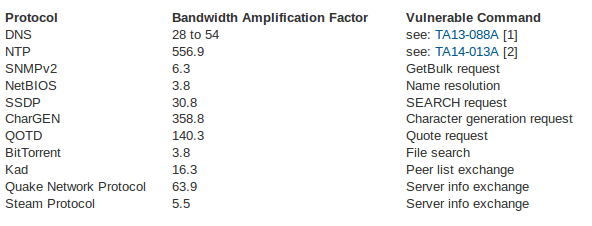
Amplification DDoS Attacks Come Again - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

A broad learning-based comprehensive defence against SSDP reflection attacks in IoTs - ScienceDirect

A broad learning-based comprehensive defence against SSDP reflection attacks in IoTs - ScienceDirect